SysRq - Linux Magic System Request Key Hacks
What is the magic SysRq key?
It is a ‘magical’ key combo you can hit which the kernel will respond to regardless of whatever else it is doing, unless it is completely locked up.
How do I enable the magic SysRq key?
You need to say “yes” to ‘Magic SysRq key (CONFIG_MAGIC_SYSRQ)’ when configuring the kernel. When running a kernel with SysRq compiled in, /proc/sys/kernel/sysrq controls the functions allowed to be invoked via the SysRq key. The default value in this file is set by the CONFIG_MAGIC_SYSRQ_DEFAULT_ENABLE config symbol, which itself defaults to 1. Here is the list of possible values in /proc/sys/kernel/sysrq:
0 - disable sysrq completely
1 - enable all functions of sysrq
$>$1 - bitmask of allowed sysrq functions (see below for detailed function description):
2 = 0x2 - enable control of console logging level 4 = 0x4 - enable control of keyboard (SAK, unraw) 8 = 0x8 - enable debugging dumps of processes etc.16 = 0x10 - enable sync command
32 = 0x20 - enable remount read-only
64 = 0x40 - enable signalling of processes (term, kill, oom-kill)
128 = 0x80 - allow reboot/poweroff
256 = 0x100 - allow nicing of all RT tasks
You can set the value in the file by the following command:
$ echo "number" >/proc/sys/kernel/sysrq
The number may be written here either as decimal or as hexadecimal with the 0x prefix. CONFIG_MAGIC_SYSRQ_DEFAULT_ENABLE must always be written in hexadecimal.
Note that the value of /proc/sys/kernel/sysrq influences only the invocation via a keyboard. Invocation of any operation via /proc/sysrq-trigger is always allowed (by a user with admin privileges).
How do I use the magic SysRq key?
Write a character to /proc/sysrq-trigger. e.g.:
$ echo "command key" > /proc/sysrq-trigger
The “command key” is case sensitive.
What are the command keys?
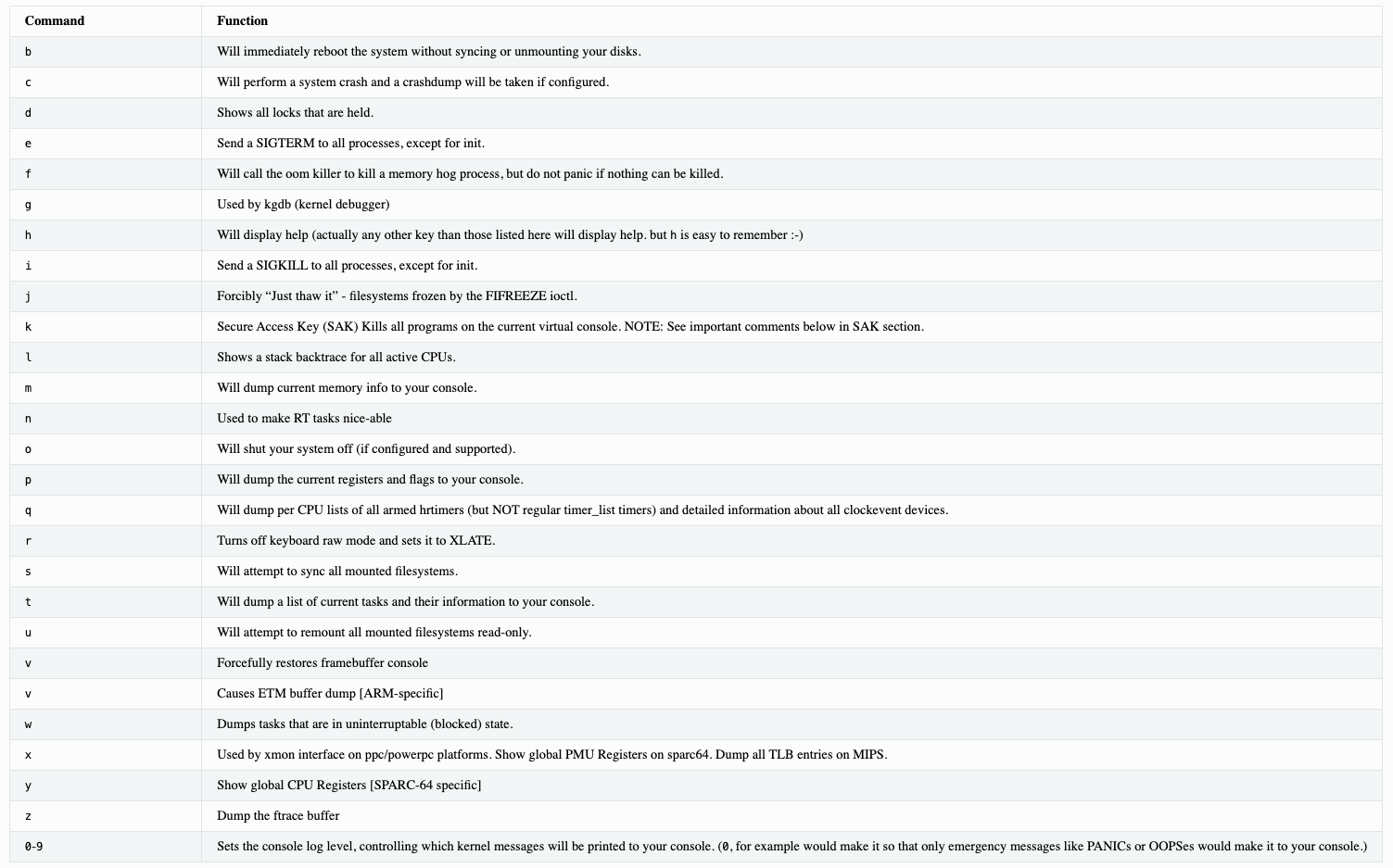
What can I use them for?
If we want to check the backtrace of all active CPUs, we can do following.
$ echo l > /proc/sysrq-trigger
$ tail -f /var/log/messages
May 21 17:49:41 host1 kernel: sysrq: Show backtrace of all active CPUs
May 21 17:49:41 host1 kernel: NMI backtrace for cpu 34
May 21 17:49:41 host1 kernel: CPU: 34 PID: 27101 Comm: bash Tainted: G O 5.7.12-1.el7.elrepo.x86_64 #1
May 21 17:49:41 host1 kernel: Hardware name: Supermicro SYS-1029U-TN12RV/X11DPU-V, BIOS 3.4 11/03/2020
May 21 17:49:41 host1 kernel: Call Trace:
May 21 17:49:41 host1 kernel: dump_stack+0x6d/0x9a
May 21 17:49:41 host1 kernel: ? lapic_can_unplug_cpu.cold+0x40/0x40
May 21 17:49:41 host1 kernel: nmi_cpu_backtrace.cold+0x14/0x53
May 21 17:49:41 host1 kernel: nmi_trigger_cpumask_backtrace+0xd9/0xdb
May 21 17:49:41 host1 kernel: arch_trigger_cpumask_backtrace+0x19/0x20
May 21 17:49:41 host1 kernel: sysrq_handle_showallcpus+0x17/0x20
May 21 17:49:41 host1 kernel: __handle_sysrq.cold+0x48/0x111
May 21 17:49:41 host1 kernel: write_sysrq_trigger+0x28/0x37
May 21 17:49:41 host1 kernel: proc_reg_write+0x66/0x90
May 21 17:49:41 host1 kernel: __vfs_write+0x1b/0x40
May 21 17:49:41 host1 kernel: vfs_write+0xb9/0x1b0
May 21 17:49:41 host1 kernel: ksys_write+0x67/0xe0
May 21 17:49:41 host1 kernel: __x64_sys_write+0x1a/0x20
May 21 17:49:41 host1 kernel: do_syscall_64+0x60/0x1e0
May 21 17:49:41 host1 kernel: entry_SYSCALL_64_after_hwframe+0x44/0xa9
<...>
The same message can also be checked from the following command.
$ dmesg -T
$ journalctl --since "5 minutes ago"