Capture and analyze network packets with tcpdump
Capture packets with tcpdump
In this example, we only capture 1000 packets(-c1000) and use IP addresses and ports(-nn) for easier analysis. The raw packets are written to file “tcpdump.1000” for further analsis.
$ tcpdump -i eth5 -c1000 -nn -w tcpdump.1000
View the packets data
We can use tcpdump to view the packets directly.
$ tcpdump -nn -r tcpdump.1000 | more
reading from file tcpdump.1000, link-type EN10MB (Ethernet)
22:42:10.018758 IP 192.168.1.18.980 > 192.168.1.16.2049: Flags [P.], seq 1:16545, ack 72, win 501, options [nop,nop,TS val 4292822374 ecr 2230894482], length 16544: NFS request xid 2912663971 16540 getattr fh 0,0/22
22:42:10.018895 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [.], ack 16545, win 9508, options [nop,nop,TS val 2230894483 ecr 4292822374], length 0
22:42:10.021125 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [P.], seq 72:144, ack 16545, win 9596, options [nop,nop,TS val 2230894485 ecr 4292822374], length 72: NFS reply xid 781957539 reply ok 68
22:42:10.021400 IP 192.168.1.18.980 > 192.168.1.16.2049: Flags [P.], seq 16545:33089, ack 144, win 501, options [nop,nop,TS val 4292822377 ecr 2230894485], length 16544: NFS request xid 2929441187 16540 getattr fh 0,0/22
22:42:10.021536 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [.], ack 33089, win 9508, options [nop,nop,TS val 2230894485 ecr 4292822377], length 0
22:42:10.023219 ARP, Request who-has 70.0.69.235 tell 70.0.193.122, length 46
22:42:10.023558 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [P.], seq 144:216, ack 33089, win 9596, options [nop,nop,TS val 2230894487 ecr 4292822377], length 72: NFS reply xid 798734755 reply ok 68
22:42:10.023844 IP 192.168.1.18.980 > 192.168.1.16.2049: Flags [P.], seq 33089:49633, ack 216, win 501, options [nop,nop,TS val 4292822379 ecr 2230894487], length 16544: NFS request xid 2946218403 16540 getattr fh 0,0/22
22:42:10.023962 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [.], ack 49633, win 9508, options [nop,nop,TS val 2230894488 ecr 4292822379], length 0
22:42:10.025962 IP 192.168.1.16.2049 > 192.168.1.18.980: Flags [P.], seq 216:288, ack 49633, win 9596, options [nop,nop,TS val 2230894490 ecr 4292822379], length 72: NFS reply xid 815511971 reply ok 68
<omitted...>
We also can view the data with wireshark GUI. We can use the filter to only display the data we are interested in. In this case, we only display the data related the ip address “192.168.1.18”. The wireshare can be installed on the desktop and open the captured packets data file.
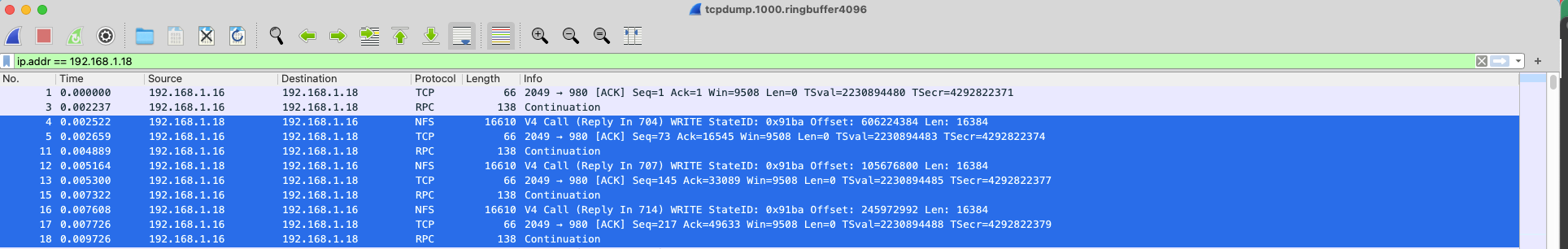
Understand the tcpdump output
The first field, 22:42:10.021125, represents the timestamp of the captured packet.
The next field, IP, represents the network layer protocol, in this case, IPv4.
The next field, 192.168.1.16.2049 > 192.168.1.18.980, is the source and destination IP address and port.
The next field, Flags [P.], represents the TCP flags. The typical values for this field include the following.
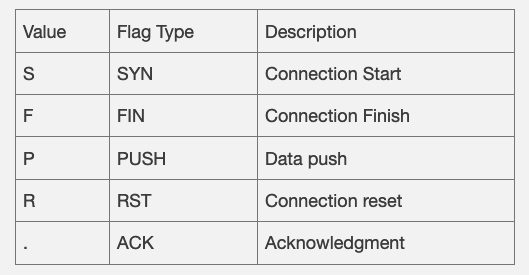
The next field, seq 72:144, is the sequence number of the data contained in the packet. It means the packet contains bytes 72 to 144.
The next field, ack 16545, is the Ack number. For the side of receiving data, this field represents the next expected byte of data. In this case, the Ack number for the next expected packet would be 16545.
The next field, win 9596, is the window size. It represents the number of bytes available in the receiving buffer.
Followed by a field, length 72, which represents the length in bytes of the data.
In the above example, the data are sending from 192.168.1.18 to 192.168.1.16. The average packet size is 16k which is sent over NFSv4.